Alpha V2ray – Tunnel VPN: A Secure and Reliable VPN Solution
Online security is paramount in today's digital landscape. Alpha V2ray – Tunnel VPN offers robust protection for individuals and businesses, safeguarding online activities from cyber threats. Its open-source nature ensures transparency and trustworthiness, allowing users to independently verify its security and privacy features. This free application avoids data misuse and unauthorized collection.
Versatile Connectivity:
Alpha V2ray supports multiple protocols (TCP, UDP, and V2ray), providing flexibility to bypass network restrictions and access otherwise inaccessible content. The advanced V2ray protocol enhances security and privacy with:
- Traffic Obfuscation: Masks VPN traffic as regular internet traffic, evading detection and blocking by network administrators and ISPs. This is crucial in regions with strict internet censorship.
- Multi-Path Routing: Uses multiple internet connections simultaneously for improved speed, stability, and reliability.
- Protocol Camouflage: Disguises itself as other protocols (HTTP/HTTPS) to further evade detection.
Unwavering Security:
Alpha V2ray employs cutting-edge encryption (AES-256 and OpenVPN) to protect all data transmitted through the VPN. This ensures data confidentiality and prevents unauthorized access.
Privacy Guaranteed:
A strict no-logs policy ensures user anonymity. No browsing history, connection logs, or personally identifiable information is stored.
High-Speed Performance:
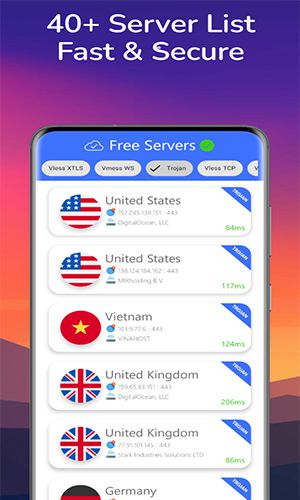
Experience fast and reliable connections, ideal for streaming, gaming, and seamless internet browsing. Servers in numerous locations guarantee optimal connectivity worldwide.
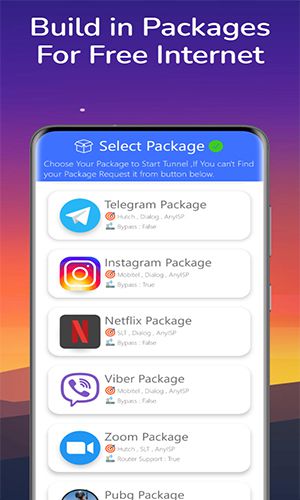
User-Friendly Design:
The intuitive interface is accessible to all users, regardless of technical expertise. Available across multiple platforms (Windows, Mac, Android, iOS), switching servers and protocols is effortless.
In Summary:
Alpha V2ray – Tunnel VPN provides a secure, reliable, and user-friendly VPN experience. Its robust security features, coupled with a no-logs policy and versatile protocols, make it a top choice for prioritizing online privacy and security.